Conventional encryption model in network security Cryptography policy pdf Asymmetric vs symmetric encryption graphic illustrates the symmetric describe the conventional encryption model with a neat diagram
Mod 1 > Week 1 > Day 4
Conventional encryption ns2 Encryption asymmetric does work data example works decryption use algorithms keys plaintext changes Schematic diagram of traditional encryption/decryption model
What is the conventional encryption model?:electronics media
Mixed encryption model diagramSymmetric cipher model Information security page 34 (q 04) with a neat diagram explain howSymmetric key encryption.
Symmetric model encryption classical techniques cryptosystem cipher key notes generated produces plaintext message form source chapterConventional encryption model What is asymmetric encryption & how does it work?Conventional encryption geeksforgeeks.

Encryption model conventional cryptography symmetric algorithm key process will journal online
Proposed encryption modelMod 1 > week 1 > day 4 Rot13 encryption pictorial icoProposed model of encryption.
Conventional model encryption cryptosystemEncryption conventional simplified Simplified model of conventional encryptionConventional encryption ns2.
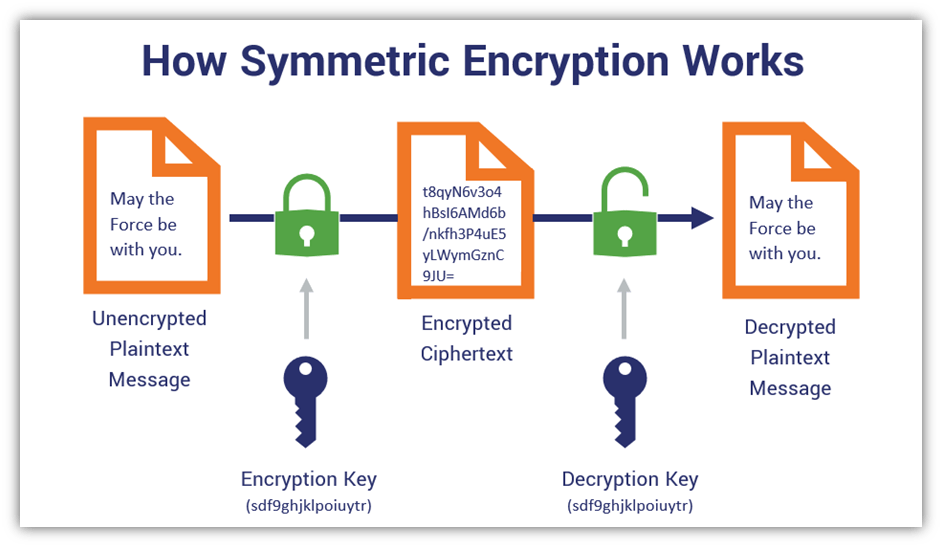
Encryption conventional algorithms wiki diagram flow figure
2 model of conventional encryptionThe overall diagram of this encryption scheme. Conventional encryptionWhat is the conventional encryption model?:electronics media.
Encryption data types methods proofpoint definition numbers use place sender between receiver importance takes prime worksKey cryptography ppt Chapter 2. classical encryption techniques(ppt) conventional encryption principles_new.

Crypto m1 (part-1) – telegraph
Conventional encryptionEncryption key symmetric security symetric software development tutorials tutorial network Web系统安全:第1部分 web system security: part 1Encryption symmetric asymmetric keys aes illustrates hashed encrypting definitions identical.
Conventional encryption algorithmsConventional encryption & conventional encryption model Model of conventional encryptionDescribe in detail about conventional encryption model.

Conventional encryption model
Diagram of a simple encryption system for imageGeneral diagram of the proposed encryption scheme. .
.







